Sécurisation Centreon : comment configurer l'accès HTTPS pour l'interface Web ?
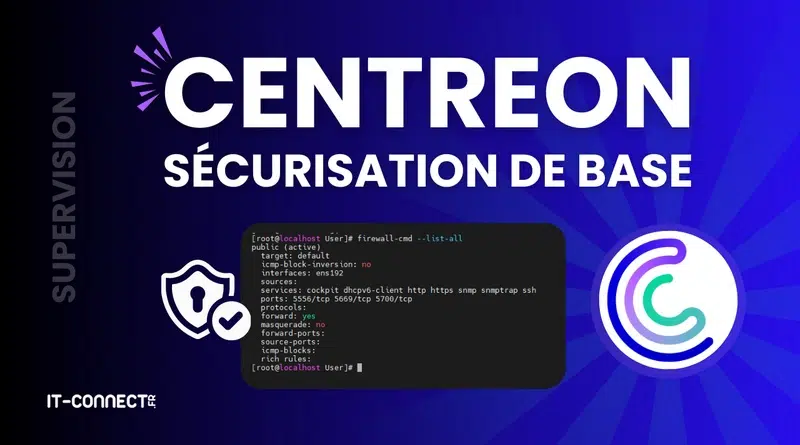
I. Présentation Dans ce tutoriel, nous allons voir comment configurer SSL/TLS sur Centreon pour passer en HTTPS, afin de protéger vos communications à l’aide de connexions chiffrées. Précédemment...